Information Gathering
First Step in Hacking
INTRODUCTION
Footprinting is an ethical hacking process of gathering information about the target and its environment.
This is a pre-attack stage and maximum efforts are deployed to ensure that the operations conducted are executed under stealth and target can’t trace back you. Footprinting is a first and the important step because after this a penetration tester knows how the hacker sees this network.
Good information gathering can make the difference between a successful pentest and one that has failed to provide maximum benefit to the client.
It includes
- Registration details of the website, contact details.
- Email harvesting,
- Finding out the target IP address and determine network range
- Identify active machine, DNS record , subdomains.
- Operating system fingerprinting.
- Finding login pages, sensitive directory
- Find out any known vulnerability for that particular version.
WHOIS Database Lookup
WHOIS allows us to access information about the target including Registration Detail, IP address, contact information containing the address, Email ID, phone number. It also also displays domain owner and domain registrar.
Email Harvesting
The theharvester tool available in Kali-Linux is an e-mail accounts, username, and hostname/ subdomains gathering tool.
As an example, if you want to find e-mail addresses and hostnames for a target domain using Google, following is the appropriate command:
#./theHarvester.py -d targetdomain -l 100 -b google
Search Engines Hacking
Marking a search query against your target in search engines (Google, Yahoo & Bing etc.) can also reveal great amount of information if used properly. Google Advance search or Google Hacking can help to locate more detailed information like company policies, employee’s details & online hidden pages etc. Google Hacking Database is a database of queries that identify sensitive information.
Traceroute
Traceroute is using UDP or ICMP ECHO to send out the packet with a Time To Live (TTL) of one, and incrementing it until reaching the target, the tcptraceroute is using TCP SYN to send out the packet to the target.
tcptraceroute will receive a SYN/ACK packet if the port is open, and it will receive a RST packet if the port is closed.
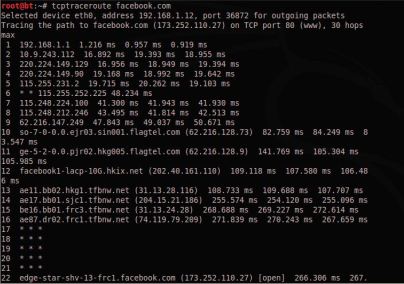
After route number 17, we are no longer able to get the route information. Usually this is because our traceroute is being blocked by a filtering device.
DNS Reconnaissance
We can interact with a DNS server using various DNS clients such as host, nslookup, dig,etc.
nslookup is a computer program used in Windows and Unix to query Domain Name System(DNS) servers to find DNS details, including IP addresses of a particular computer, MX records for a domain and the NS servers of a domain. The name nslookup means “name server lookup”.

The above image explains that we connected to local server and asked to resolve a record for us. The server responded with the IP address of the victim.
Before going ahead try to understand some DNS records. For more details please visit https://en.wikipedia.org/wiki/List_of_DNS_record_types
– A – Points to host IP address
– MX – Points to domain mail server.
– NS- Points to host name server
– CNAME-Canonical naming allowing aliases to host.
– SOA- Indicate authority for domain.
– SRV-Service Record.
– PTR-Maps IP address to hostname.
– RP-Responsible Person.
– INFO- Host Information.
– MX – Points to domain mail server.
– NS- Points to host name server
– CNAME-Canonical naming allowing aliases to host.
– SOA- Indicate authority for domain.
– SRV-Service Record.
– PTR-Maps IP address to hostname.
– RP-Responsible Person.
– INFO- Host Information.
In order to retrieve mail server information we can use the following commands
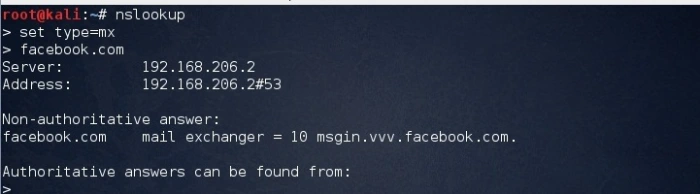
While gathering information can divided into 3 main techniques:-
- Forward lookup bruteforce
- Reverse lookup bruteforce
- Verifying SPF Record
- Zone transfers
1. Forward lookup bruteforce
The main idea behind this technique is to guess correct valid server names of organization. We can try this using the host command. The output gave us an IP address of the server.
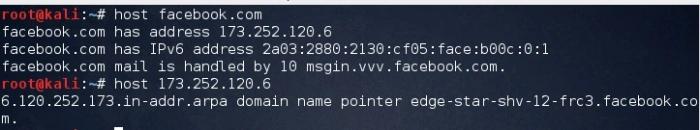
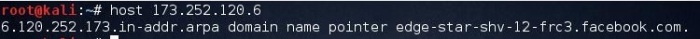
2. Reverse lookup bruteforce
This is a technique which is reverse to forward lookup bruteforce, in this case victim’s IP address is known and we need to find the server names and other information pertaining to the organization.
3. Verifying SPF Record
An SPF record is a TXT record that is part of a domain’s DNS zone file. The TXT record specifies a list of authorized host names/IP addresses that mail can originate from for a given domain name.
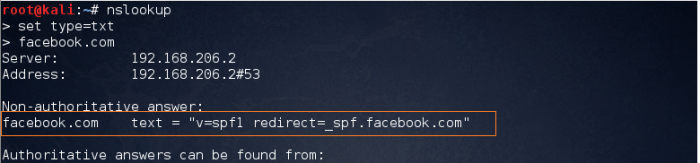
The purpose of an SPF record is to prevent spammers from sending messages with forged From addresses at your domain.
4. Zone transfers
DNS Zone Transfer is generally used for DNS database replications and backups. The security problem with DNS zone transfer is that it can be used to decipher the topology of a company’s network. Specifically when a user is trying to perform a zone transfer it sends a DNS query to list all DNS information like name servers, host names, MX and CNAME records, zone serial number, Time to live records etc. Due to the amount of information that can be obtained DNS zone transfer cannot be easily found in nowadays.

The above image shows the how to get the dns server names.
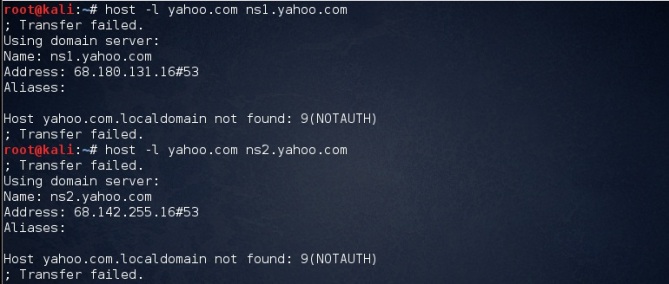
As the response to our query is been failed thus we can say that zone transfer is configured properly
CONCLUSION
Hopefully this article has demonstrated some of the ways in which passive reconnaissance can be useful as part of your security testing activities. It’s obviously not a replacement for active testing and only scratches the surface when it comes to discovering vulnerabilities but it can certainly provide some valuable information to help scope your testing efforts.















contact elizabethjone146@gmail.com
ReplyDeleteWhatsApp +18572012269
Do you need a hacker to hack into your cheating ass account or do you want us to hack into the following account such as.
1-facebook hack
2-gmail hack
3-whatsapp hack
4-website hack
5-tracking calls
6-online hacking lectures
7-phone clone
8-online records changes
9-retrival of hacked social media account
10 ATM merchine hack/password from any Email Address.
11 Get any password from any Facebook, Twitter or Instagram account.
12 Cell phone hacking (whatsapp, viber, line, wechat, etc)
13 Grades changes (institutes and universities)
14 Websites hacking, pentesting.
15 IP addresses and people tracking.
16 Hacking courses and classes.
17 blank ATM CARD.
contact elizabethjone146@gmail.com
BEST WAY TO HAVE GOOD AMOUNT TO START A GOOD BUSINESS or TO START LIVING A GOOD LIFE….. Hack and take money directly from any ATM Machine Vault with the use of ATM Programmed Card which runs in automatic mode. email (williamshackers@hotmail.com) or WhatsApp +27730051607.
ReplyDeletefor how to get it and its cost . ………. EXPLANATION OF HOW THESE CARD WORKS………. You just slot in these card into any ATM Machine and it will automatically bring up a MENU of 1st VAULT $200 $300 $500, $1,000, 2nd VAULT $2,000, $3000, $4000 RE-PROGRAMMED, EXIT, CANCEL. Just click on either of the VAULTS, and it will take you to another SUB-MENU of ALL, OTHERS, EXIT, CANCEL. Just click on others and type in the amount you wish to withdraw from the ATM and you have it cashed instantly… Done. ***NOTE: DON’T EVER MAKE THE MISTAKE OF CLICKING THE “ALL” OPTION. BECAUSE IT WILL TAKE OUT ALL THE AMOUNT OF THE SELECTED VAULT. email (williamshackers@hotmail.com) or WhatsApp +27730051607.